We are the MAIS (Microarchitecture and Artificial Intelligence Security) Group led by Dr. Berk Gulmezoglu in Electrical and Computer Engineering (ECpE) Department at Iowa State University.
Recent News:
- [Mar 25] Seonghun has received an ASPLOS Travel Grant. Thank you, ASPLOS committee!
- [Mar 25] Debopriya has been awarded the Takano Scholarship, which covers his tuition and salary for one year. We appreciate the support of the Electrical and Computer Engineering (ECpE) Department. Congratulations Debopriya!
- [Feb 25] Seonghun Son will have a summer internship at Seagate. Congratulations Seonghun!
- [Feb 25] Our paper “SMaCk: Efficient Instruction Cache Attacks via Self-Modifying Code Conflicts” got accepted at ASPLOS ’25. Congratulations Seonghun! Thank you for all the support given by our collaborator, Daniel Moghimi, at Google! AMD has published a security bulletin for our attack.
- [Jan 25] Two papers got accepted to the International Conference on Transportation & Development (ASCE). Congratulations Rajrup and Kunle!
- [Jan 25] We have recently received the SFS NSF Grant ($3.7M). The project title is “CyberCorps Scholarship for Service: Training Iowa’s Cyber Talents to Protect the Nation’s Critical Infrastructure” with Dr. Doug Jacobson (PI) and Dr. Manimaran Govindarasu (co-PI).
- [Jan 25] Dr. Gulmezoglu will give an invited talk online for the University of North Dakota on Jan 9. Please see the flyer if you are interested in joining the talk!
- [Nov 24] Our poster, “DefWeb: Defending User Privacy against Cache-based Website Fingerprinting Attacks with Intelligent Noise Injection (PDF),” got the best poster award at the Midwest Security Workshop 2024 organized at Purdue University. Congratulations Seonghun!
- [Oct 24] Our paper “Systematical Evasion from Learning-based Microarchitectural Attack Detection Tools” got accepted at IEEE JETCAS. Jonathan participated in this project as an undergraduate student. Congratulations Debopriya and Jonathan!
- [Sep 24] Seonghun Son and Debopriya Roy Dipta have been invited to participate in the CAE-R Symposium in St Louis. They will present research posters and give a dissertation talk on October 10.
- [Sep 24] Dr. Gulmezoglu has received a grant as a co-PI from Flight Aviation Administration (FAA) to work on the “Machine Learning usage on Drone Capture Image Analysis on Airports” with Dr. Halil Ceylan (PI), Dr. Sunghwan Kim, Dr. Yunjeong Mo, Beena Ajmera, In-Ho Cho, Wensheng Zhang, and Dr. Colin N. Brooks.
- [Aug 24] Dr. Gulmezoglu has been invited to the Program Committee of USENIX Security Conference 2025.
- [Aug 24] Dr. Gulmezoglu has received a grant as a co-PI from Iowa DOT to work on the “Usage of Drones for Iowa Transportation and Infrastructure Work” with Dr. Halil Ceylan (PI), Dr. Sunghwan Kim, Dr. Yunjeong Mo, and Dr. Colin N. Brooks.
- [Aug 24] Seonghun Son will give an invited talk on “Microarchitectural Security and Machine Learning Security for Reliable Autonomous Driving Systems” at Kyungpook National University.
- [Aug 24] One team paper, “Ain’t How You Deploy: An Analysis of BGP Security Policies Performance Against Various Attack Scenarios with Differing Deployment Strategies,” written during the INSURE Workshop at ISU, has been accepted to the ISNCC conference. Congratulations Seth, Calvin, German, and Andrew!
- [Jun 24] INSURE Summer Research Workshop is starting with 12 students from different states today!
- [Apr 24] Our paper “Dynamic Frequency-Based Fingerprinting Attacks against Modern Sandbox Environments” in collaboration with Telefonica Research and University of Lubeck is accepted at Euro S&P 2024!
- [Mar 24] We will host Summer INSuRE+E Research Workshop at Iowa State University between June 10-28. More details coming soon!
- [Mar 24] Our poster on the security of Machine Learning models, in collaboration with NSA, is accepted to the CAE symposium. Seonghun will present the poster in Kentucky. Congratulations team!
- [Jan 24] Debopriya is awarded the Sellers Scholarship for the academic year 2023-2024. Congratulations Debopriya!
- [Dec 23] Our paper “DefWeb: Defending User Privacy against Cache-based Website Fingerprinting Attacks with Intelligent Noise Injection” is accepted at ACSAC 2023. Seonghun presented our paper in Austin!
- [Sep 23] Dr. Berk Gulmezoglu is selected as one of the participants for the “CAE-R SPECIAL TOPICS WORKSHOP ON GENERATIVE AI TOOLS AND CYBERSECURITY” in Chicago.
- [May 23] Dr. Berk Gulmezoglu will attend NSF/SaTC Aspiring PI Workshop 2023 in Washington, DC.
- [May 23] Our paper “MAD-EN: Microarchitectural Attack Detection through System-wide Energy Consumption” is accepted at IEEE Transactions on Information and Forensics Security. Congrats Debopriya!
- [Dec 22] Our paper “Overcoming the Pitfalls of HPC-based Cryptojacking Detection in Presence of GPUs” in collaboration with University of Lubeck is accepted at ACM CODASPY 2023. Congratulations Claudius!
- [Dec 22] Debopriya presented his paper “DF-SCA: Dynamic Frequency Side-Channel Attacks are Practical” at ACSAC 2022.
- [Oct 22] Debopriya got selected for ACSAC Student Conferenceship 2022. Thank you ACSAC Student Conferenceship committee for the support!
- [Oct 22] Our paper “DF-SCA: Dynamic Frequency Side-Channel Attacks are Practical” is accepted at ACSAC 2022! This is Debopriya’s first publication in his PhD journey. Congratulations Debopriya!
- [Sep 22] Our work-in-progress paper “WiP: MAD-EN: Microarchitectural Attack Detection through System-wide Energy Consumption” is accepted at HASP 2022!
- [Aug 22] Dr. Gulmezoglu gave an invited talk on “The Security Implications of Dynamic Frequency on Intel, AMD, and ARM Devices” at Worcester Polytechnic Institute.
- [Jul 22] Debopriya gave an invited talk on his recent paper (DF-SCA: Dynamic Frequency Side-Channel Attacks are Practical) at NVIDIA.
- [Apr 22] Our lab’s undergraduate research student Anuraag Pujari’s presentation on “Security Analysis of Recurrent Neural Network Algorithms under Microarchitectural Attacks” have been accepted at NCUR 2022. Congratulations Anuraag!
- [Dec 21] Our paper “XAI-based Microarchitectural Side-Channel Analysis for Website Fingerprinting Attacks and Defenses” is accepted at IEEE Transactions on Dependable and Secure Computing Journal
- [May 21] Our paper “Fastspec: Scalable generation and detection of spectre gadgets using neural embeddings” is accepted at EURO S&P 2021!
Our research is based on discovery of new microarchitectural leakages and analyzing side-channel data with Deep Learning algorithms. We are currently working on the broad range of microarchitectural attacks on AMD, Intel and ARM devices. New attacks and detection techniques are developed to increase the awareness of industry on the potential of side-channel attacks.
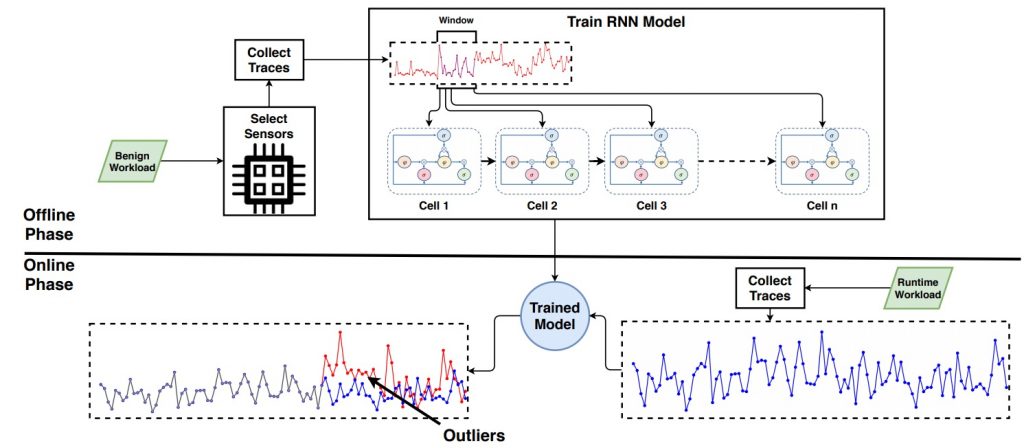
FortuneTeller: Detecting Microarchitectural Attacks via Deep Learning
Ongoing Projects
- Microarchitectural attack detection using Deep Learning based techniques: Since microarchitectural attacks were introduced, number and variety of the attacks have increased tremendously in the last decade. Hence, chip vendors such as Intel, AMD, ARM have difficulties to come up with patches in a short time. Until these patches become available to customers, attackers have a time period to exploit individual devices through novel side-channel attacks. This project aims to develop new low overhead detection mechanisms to protect the commercial servers and personal computers in real time. Especially, with the advanced learning capabilities of Deep Learning algorithms, it has become possible to train large-scale models to detect side-channel attacks. Therefore, we train various Deep Learning models to compare the efficiency of algorithms and discover new ways to identify ongoing side-channel attacks on the devices.
- Discovering new leakage sources in Intel and AMD architectures: Chip vendors are in a competition to establish the best performance to their customers for a long time. To increase their chip’s performance, they introduce new features such as larger cache sizes, speculative and out-of-order execution mechanisms and so on. While these features provided a large performance gain, they have also become targets for microarchitectural attacks. Especially with Spectre and Meltdown attacks, the potential destruction of microarchitectural attacks is more obvious. Thus, it is more important than before to identify the leakage sources and attacker capabilities before they are exploited by malicious people. This project aims to analyze the architectural components in Intel and AMD devices and discover new ways to leak personal information. Moreover, we focus on several hardware countermeasures to protect confidential information leakage.
- Profiling-based side-channel attacks on CPU and GPU systems: Once new attacks are discovered, side-channel data is collected to obtain a meaningful information about targeted victim. The information extraction mostly requires experts to implement side-channel data analysis techniques such as DPA, template attacks etc. This project focuses on new side-channel analysis techniques to extract maximum information from side-channel data. The analysis techniques can also be developed by implementing newest Deep Learning techniques.